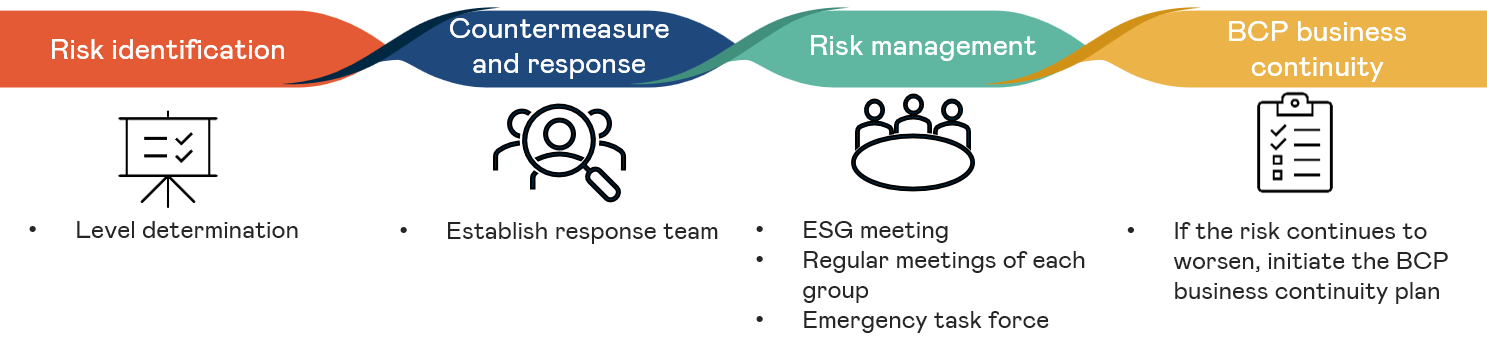
Risk management
Establish company-level systematic risk response policies and processes to effectively grasp the risks of the enterprise.
The risk governance team under the enterprise's internal ESG committee is responsible for the risk identification operation of the entire company. Through the participation of units including product R&D, manufacturing, sales, finance, legal, human resources, information system, and environmental safety management, in addition to mitigation response, they should also seek corresponding opportunities.
Business continuity management plan
The objective of AUO Crystal is business continuity, to continue to focus and invest resources to conduct risk control and response preparations for the potential risks of the various internal and external incidents that affect the operation of this company. Business Continuity Plan (BCP) is a part of management. It helps enterprises maintain key operational activities at acceptable preset levels when incidents occur. The enterprise has already formulated drills and risk management strategies for fire, earthquake, chemical leakages and other incidents, and will continue to perfect the BCP response capabilities for different scenarios in the future.
Information security
Information security policy
In order to ensure the company’s intellectual property, customer data and to improve the information security awareness of employees, AUO Crystal formulated information security policies as the guidelines to follow for information security management, and the various internal units assign information security officers to promote and implement the various information security governance, risk management and regulatory compliance.
- Protect customer data and the intellectual property of the company
- Strengthen information security environment and incident response capabilities
- Conduct information security audits regularly to ensure that information security policies are implemented properly
- Train all employees to implement information security protection tasks of colleagues
- Establish information security policy metrics
Information security management solutions
- Asset management: Includes hardware equipment and software licensing; must be approved before they can be installed and used.
- Account permission management: Provide different permissions according to user levels.
- Operating system hotfix and virus signature update management: Perform security updates regularly and lower the risk of virus spreading.
- Firewall and network communication management: Block external attacks, filter harmful URLs, restrict remote access permissions.
- Disaster recovery and off-site backup management: Establish response and recovery plans and strengthen corporate risk tolerance.
- Information security training: Promote information security rules regularly, hold social engineering scam drills, and improve the information security awareness of employees.